Vulnerability assessment
Track all vulnerabilities on every system to ensure your infrastructure is always secure.
Get detailed information on all the assets and vulnerabilities. Severity classification included.
Continuously detect vulnerabilities and remediate before the critical point.
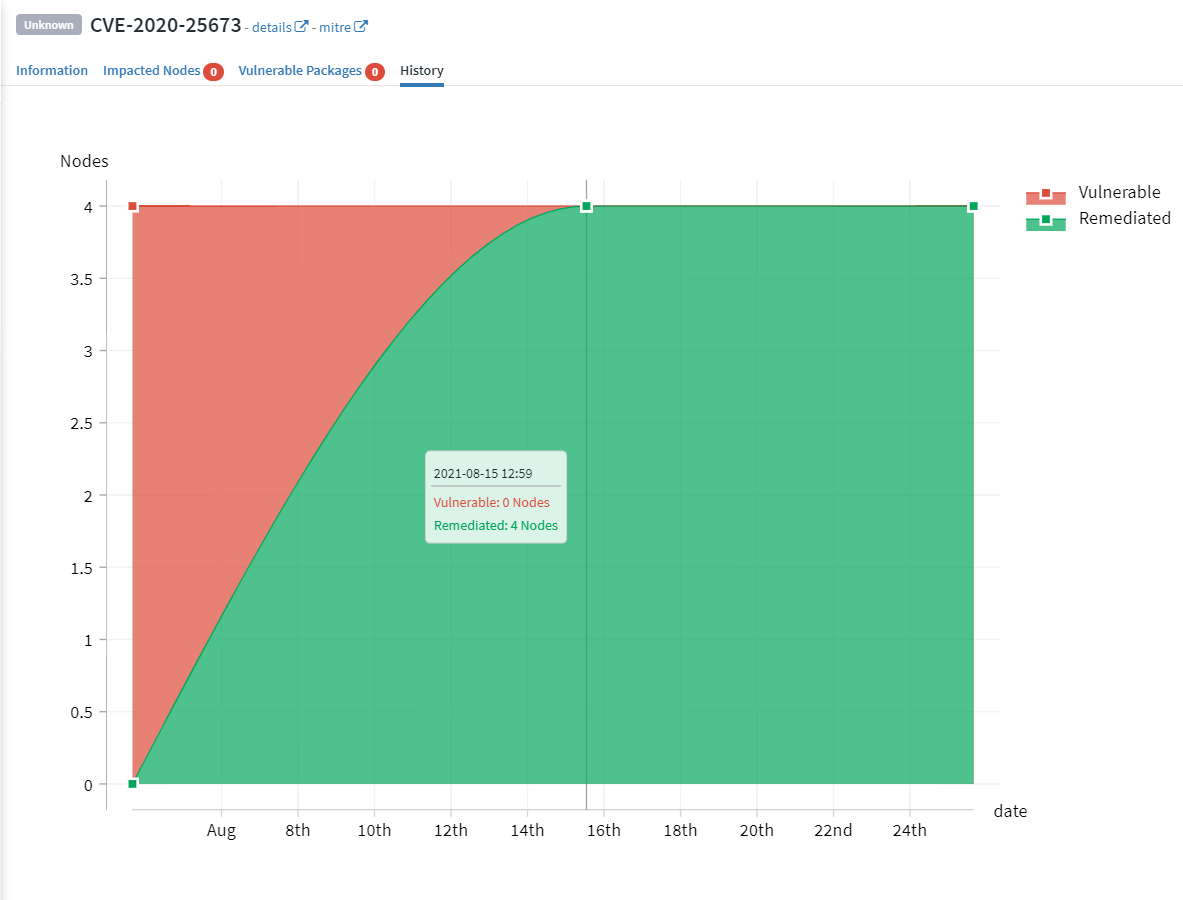
Show vulnerabilities and remediation state with specific reports.
Automate continuous vulnerability scanning
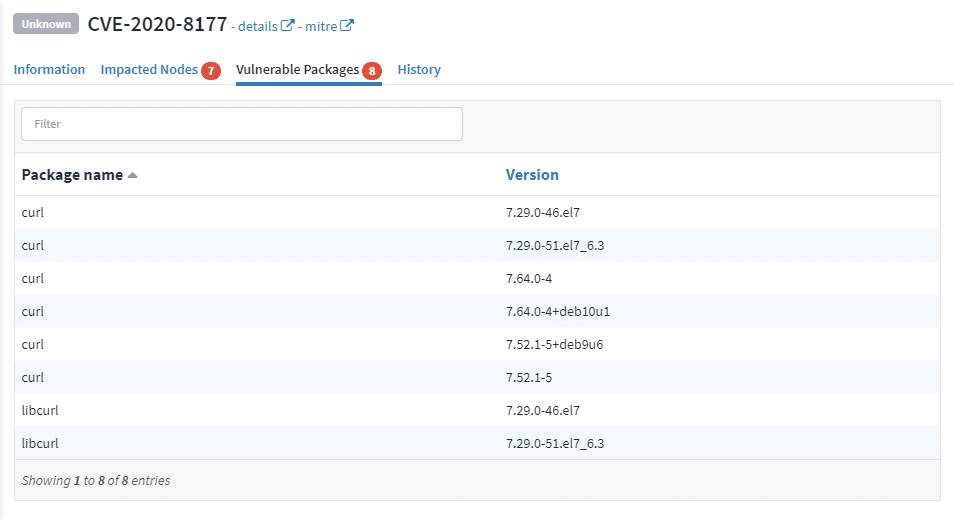
Rudder helps you manage all the vulnerabilities on your systems: CVEs (Common Vulnerabilities and Exposures) but also custom vulnerabilities that you define to prevent risks. Scans run continuously from the central server to analyze all systems and find which packages are vulnerables. This ensures a low footprint on the managed systems.

Click on the image to zoom in
Real-time details for remediation
Get real-time check results to see which systems are impacted. You can filter them by vulnerability or by system. In any case, CVE details are displayed, such as the vulnerability severity and state, to give you everything you need to plan and prioritize their remediation.
Main features
- CVE management
- Continuous assessment
- Complete inventory