Be always compliant and make your standards audits a non-event
Make sure that external regulations and internal policies required by your organization are continuously compliant within your IT infrastructure.
Switch to automatic mode for your standards compliance
Most organizations must conform to industry best practices listed in standards such as ISO 27001, PCI-DSS, CIS Benchmarks, NIST, NIS2 etc. Some also define their own internal policies. So IT teams need to ensure that the infrastructure is compliant with these standards. But auditors and security teams expect a solid and tracked implementation, while the ops teams are already fully occupied with business projects and production rollout.
Rudder provides the necessary automation, monitoring and visibility that will keep all the teams satisfied with a policy-as-code approach.
Using continuous audit and Rudder Score, identify in real time which systems are no longer compliant.
No need to manually prepare an external audit, everything is automated with Rudder.
Share dashboards and detailed reports with security teams, management and even external auditors.
Provide proof of your IT infrastructure's compliance at any time
Define your security policies
- Easily configure security policies based on your organization’s requirements
- Get help integrating standards and best practices such as CIS Benchmarks
- Benefit from the power of a compliance-as-code software with a full graphical experience
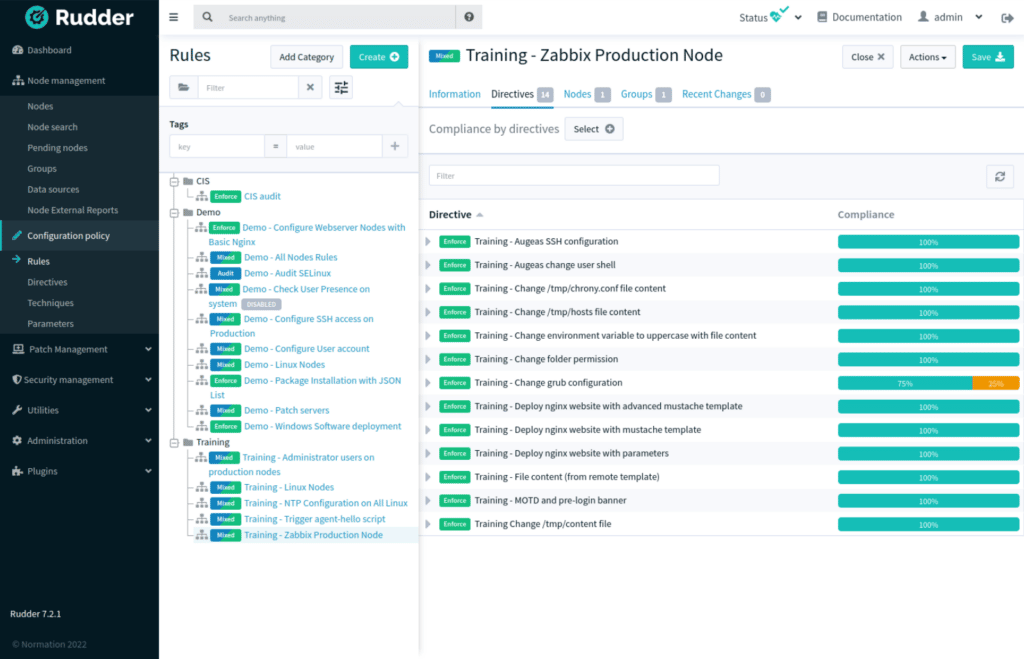
Audit, control and remediate continuously
- Take advantage of an automated audit every five minutes to ensure full compliance of your security policies
- Identify which systems no longer meet the baseline requirements
- Automatically remediate if necessary
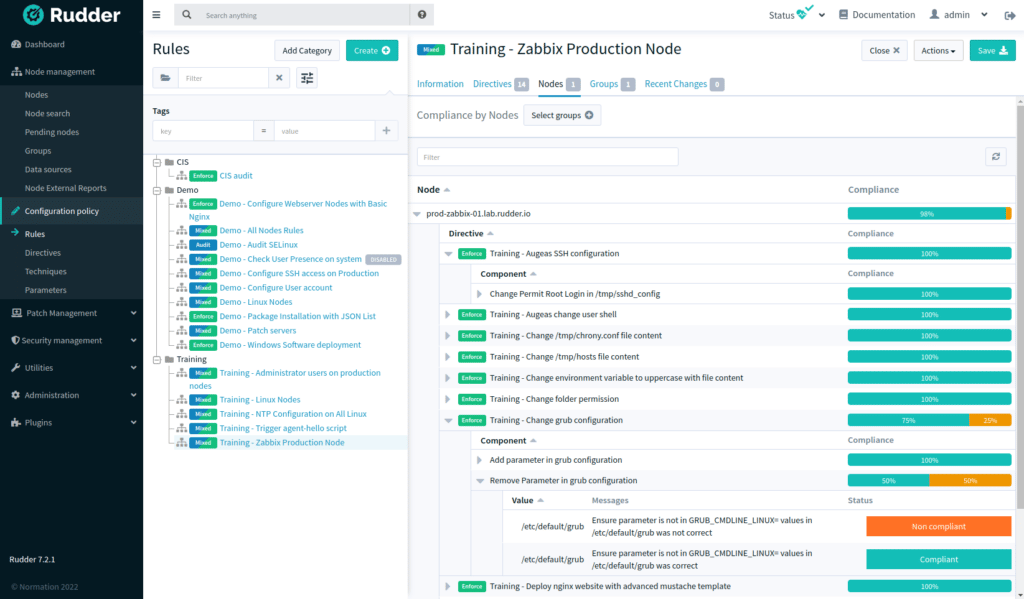
Instant view and shareable reports
- Get a global and detailed visibility of your compliance with Rudder Score and compliance views
- Monitor standards compliance over time
- Export compliance reports to prove your assessments and share them with other teams like security teams
Efficient features to simplify your standards compliance management
Custom security policies
Easily create and customize security policies through a user-friendly interface. You can manage internal security policies of your organizations, standards (ISO 27001, PCI-DSS…) and system hardening.
Audit security standards
Audit security standards with Rudder such as CIS benchmarks, SecNumCloud, etc. And check system compliance.
OpenSCAP audit
Automatically trigger OpenSCAP audits, then collect and make the results available directly in Rudder interface.
Rudder Score
Easily understand and visualize the health of your systems by aggregating Rudder components into an overall score.
Compliance view
Get an overview of your infrastructure’s configuration and security compliance. You can also view compliance for each Rudder component (by system group, by system, by rule…).
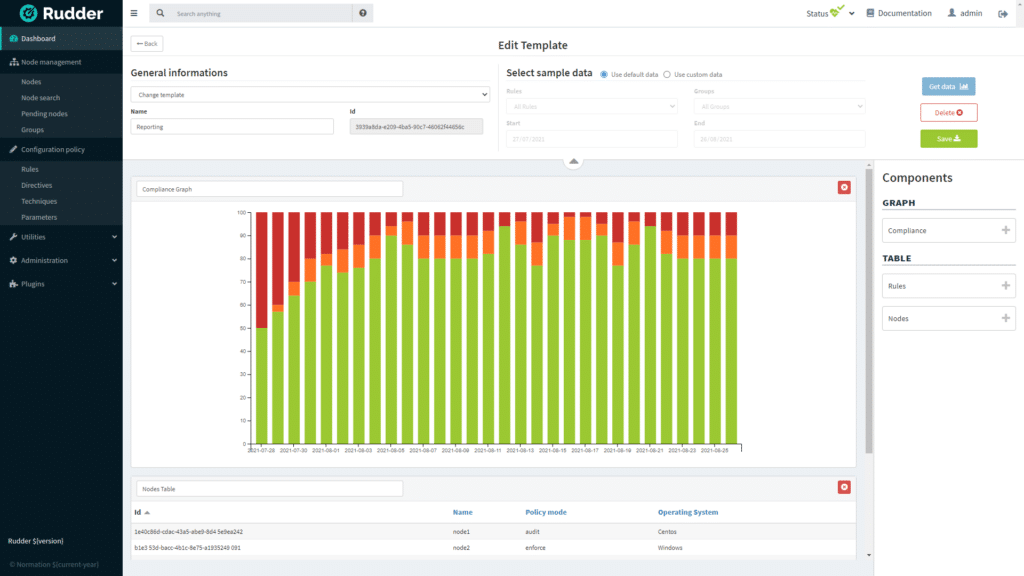
Reporting
Create and export visual reports about infrastructure compliance. Report templates can be customized.
Benefit from the expertise of our team
Interested?
Manage all your OS in one place
Rudder supports all major operating systems to help manage and control your entire IT infrastructure.








